In recent years «beneficial ownership transparency» has ceased to be a narrow compliance term and has turned into a board-level topic. By 2026, against the backdrop of the EU AML package 2021–2026, the tightening of AMLD6 and global pressure from the FATF, companies, banks and payment providers are restructuring processes as if oversight will become total tomorrow.
My experience has shown: those who do not fight the trend but design business processes with UBO realities in mind come out ahead. EU beneficial owner registers, UBO registration rules when forming a legal entity in the EU, information exchange between jurisdictions: all of this has ceased to be «paper» bureaucracy. It is the very core of the operating model on which access to banking services, onboarding speed, the ability to obtain licenses and expansion into new markets depend.
Who is a UBO and why are thresholds needed?

Ultimate Beneficial Owner (UBO): the ultimate beneficial owner who ultimately controls a company through direct ownership or beneficial interest. The traditional ownership threshold of 25% is often used by banks and beneficial ownership registers abroad, but in the EU we increasingly see a 10% threshold for UBOs in cases of heightened risk or in the context of specific sectors. A threshold does not exempt from the analysis of control: the right to appoint management, veto rights, shareholder syndicates and agreements — all of these create a beneficial interest, even if shares are split.
Complex ownership structures and UBOs: my daily reality. Trusts and foundations, nominee shareholder arrangements and nominee directors, remnants of historical mechanisms like bearer shares (which are de facto prohibited), these are all layers that compliance peels away one by one. The practice of COREDO confirms: if a structure looks “too neat”, the bank will immediately raise the bar: enhanced due diligence (EDD) is inevitable.
UBO Registers 2026
UBO register 2026: not just a date on the calendar, but a milestone when registers and banks must speak the same data language. EU countries have different models: public vs closed UBO registers, trust structures (trust registers), corporate registers, and interoperability via the Beneficial Ownership Data Standard (BODS) and the Open Ownership initiative. In the UK Companies House is strengthening quality control, in Estonia and Cyprus registers are already integrated into KYC pipelines, while in Singapore and Dubai the emphasis shifts to lawful access by authorized persons and regular updates.
GDPR and the legal limits on the publicity of registers: a constant balance. Regulators are expanding the lawful basis for access to UBO data for banks, auditors and corporate service providers (CSPs), but require strict access controls and protection of personal data. National AML competent authorities and
financial intelligence units (FIUs) receive priority access for investigations, and corporations must justify every request.
UBO Registers and the Fight Against Money Laundering
FATF recommendations on ownership transparency have established the standard: without a reliable register of ultimate beneficial owners, AML processes do not work. The Common Reporting Standard (CRS) and OECD initiatives on company transparency have completed the picture, where corporate registers, tax data and banks’ KYC converge into a single mosaic-style verification. World Bank promotes infrastructure solutions for beneficiary registration, while OpenCorporates and data aggregators speed up cross-verification of UBO registry data.
COREDO’s practice confirms: a UBO register and information exchange between jurisdictions via TIEA and MLA are not theory but a tool for «rapid tracing» of control, especially in M&A transactions and when entering new markets. We regularly see how open-access registers vs restricted-access ones differently affect the speed of banks’ Due Diligence of UBOs and the risk of de-risking clients from offshore jurisdictions.
How banks verify UBOs in offshore jurisdictions

KYC and UBO: the combination without which you won’t be able to open an account or keep correspondent banking relationships. Bank UBO due diligence includes checking UBOs in offshore jurisdictions: banks use methods to verify beneficiaries through registers, requests to CSPs, independent sources, sanctions regimes and lists, PEP screening and adverse media. When a structure includes trusts and foundations, beneficiary verification for trusts and foundations requires a named breakdown of beneficiary classes and protector roles.
Correspondent banking and UBO risks increase the requirements of local banks. If a client’s core business is linked to offshore jurisdictions, enhanced due diligence (EDD) is often triggered and even case-by-case approval with the bank’s financial intelligence function required. The COREDO team has repeatedly encountered de-risking of clients from offshore jurisdictions: banks prefer to refuse a high-risk profile rather than bear compliance costs and the threat of fines for non-compliance with AMLD6 and sanctions rules.
Requested documents and evidence

How do banks verify UBOs in offshore jurisdictions? At the core is a chain of documents: articles of incorporation, shareholder registers, trust declarations, director appointment minutes, certificates of good standing, CSP letters about nominee structures, and confirmations of the renunciation of bearer shares. Which documents prove the UBO in offshore jurisdictions? It always depends on the jurisdiction, but the single principle is the same: documentary continuity from the legal entity to the ultimate beneficiary with verified identity.
Document-based identification and identity proofing include biometric verification and digital IDs where eIDAS and local law allow. Banks require consent for data processing in accordance with the GDPR, as well as additional forms for sanctions screening. Our experience at COREDO has shown that a concise “structure map” and a checklist of beneficiary roles speed up onboarding and reduce the likelihood of repeated requests.
ETL pipeline and graph databases
Automating UBO checks for banks is impossible without integrating UBO registries into banks’ KYC pipelines. API tools for accessing UBO registries, APIs for exchanging registry data and real-time screening of UBO registries provide an advantage in time to onboard and reduce false positives/false negatives in checks. The solution developed at COREDO for one of the partner banks built an ETL pipeline for UBO registries with data quality validation, storage of data provenance and multi-stage source verification.
Graph analysis of company ownership and link analysis for detecting UBOs is my favorite part. Graph databases (for example, Neo4j) make it possible to visualize chains of dozens of entities and detect fraud analytics and shell structures. Machine learning helps with entity matching and fuzzy matching, and blockchain for storing provenance data improves audit immutability. Such a stack reduces MTTR on compliance cases and increases TPR with controlled FPR: metrics that CFOs understand without translation.
Metrics and ROI of AML technologies
Any technology is worth exactly as much as the savings it delivers or the risk it reduces. The costs of implementing UBO procedures in a bank and the compliance cost per customer should be compared with ROI metrics: reduction in time to onboard, decrease in operational hours spent on repeat requests, reduction in the number of SARs (suspicious activity reports) without loss of quality, and increased case throughput. The COREDO team implemented an ROI calculation model where we link the operational scalability of AML processes to business volume and correspondent relationship uptime.
Tuning of transaction monitoring rules and algorithms for prioritizing UBO checks helps eliminate bottlenecks in compliance queues. Compliance automation: RPA and workflows create repeatability and version control of playbooks. When the task is scaling AML processes for multinational companies, unified data quality control and data reconciliation (entity resolution) between systems deliver the real economies of scale.
Regulatory framework: standards and penalties
Compliance with AMLD5, AMLD6 and UBO registers is a mandatory requirement for lawful operation in the EU, as is compliance with the CTA (Corporate Transparency Act) for entities with a U.S. presence. Legal sanctions for failing to disclose UBOs include substantial fines, license suspensions and restrictions on banking services. In the UK and some EU jurisdictions there are already criminal penalties for deliberate falsification of ultimate beneficial owner information.
The UBO register and sanctions lists are a pairing that banks check daily. The bad news: sanctions regimes are updated unevenly; the good news: UBO monitoring practices in banks for 2026 already incorporate adverse media and PEP flags into unified screening frameworks. COREDO’s practice confirms: companies that document data provenance and best practices for documenting UBO sources more easily meet regulatory inquiries and respond to audits without stress.
COREDO case studies: solutions to complex challenges
First case: a fintech group entering the EU through a payment services license in Cyprus. The client came with a complex ownership structure involving a trust and two holding companies in different Asian jurisdictions. The COREDO team built an ownership graph, assessed the reliability of UBO data, and prepared compliance playbooks for UBO checks. Result – Licensing was completed on time, and the acquiring bank reduced time to onboard by 40% thanks to a pre-agreed document package and an EDD dossier.
Second case, a crypto provider opening an office in Estonia with subsequent expansion to the UK and Dubai. Registering UBO when forming a legal entity in the EU required alignment with the FCA’s AML registration requirements and with VARA rules in Dubai. The solution developed at COREDO included automation of KYC and UBO checks via API, entity matching with EU beneficiary registries and negative news. The client avoided de-risking of clients from offshore jurisdictions, as the banking dossier contained justification of control and a renunciation of nominee structures.
Third case: M&A with an offshore target asset and correspondent banking risks. We performed due diligence on the M&A involving an offshore target, built link analysis, identified nominee owners at the level of the second holding and proposed a restructuring to fall below the 10% UBO threshold in the EU with disclosure of the actual controller. This removed the risk of the deal being blocked by correspondent banks and reduced the cost of insuring representations and warranties.
Preparing a company for a bank UBO request
First – an ownership structure map showing all beneficial interests. Include shareholdings, control rights, shareholders’ agreements, trust documents and confirmations of the roles of protector and settlor. Second – a KYC package for each UBO: proof of identity, address, source of funds confirmation, PEP status and adverse media results. Third – a policy for monitoring changes in ownership structure and UBOs with an SLA for data updates and procedures for notifying the bank.
How to avoid mistakes when declaring UBOs? Do not rely on generalizations and “umbrella” formulations. Specify thresholds, disclose concerted actions and avoid nominee terminology without explanations. If foundations and offshore legal structures are present: attach legal opinions on the nature of control and beneficial interest, as well as letters from the CSP. At COREDO we implement checklists that minimize the risk of bank rejections.
Registry data quality: normalization
Cross-checking UBO registry data is a mandatory practice. I recommend building parsing and normalization of registry data followed by entity matching and fuzzy matching, and then reconciling with the client’s internal data and open sources like OpenCorporates. Data quality and source validation reduce the risk of false positives, and documented data provenance makes it easier to respond to regulatory requests.
Integrating UBO registries into banks’ KYC pipelines via API increases speed. Still, do not forget about access control and personal data protection: set up a lawful basis for access to UBO data and an access revocation procedure. In some jurisdictions, part of the data is available only upon request from authorized persons – the COREDO team prepares such requests in advance and factors in a buffer in project plans.
Compliance: What to monitor at the C-level
Best practices for UBO verification for C-level: regular reports with performance and risk metrics. Include MTTR for compliance cases, FPR/TPR for screening, time to onboard, the number of cases in EDD and the share of structures with trusts and nominees. Add a cost-benefit analysis of implementing UBO registries and ROI metrics: reduction in cost per client, preserved correspondent relationships and the speed of opening bank accounts.
Practical steps for the CFO when assessing UBO risk: classify jurisdictions by EDD complexity, create a catalog of CSPs and company formation agents with a reliability rating, and create a map of sanctions linkages. The COREDO team implemented an owner risk-scoring model for a multinational client, where machine learning and graph features improve the accuracy of prioritizing UBO checks and reduce the load on the EDD team.
Linking the UBO to the actual operation
When you register a legal entity in the EU, bear in mind that the UBO register is often synchronized with bank onboarding. This means that mistakes at the UBO registry stage will surface when opening an account and when obtaining licenses: crypto, forex,
payment services, and in some jurisdictions, banking licenses as well.
COREDO’s practice confirms: early alignment of UBO and licensing requirements saves weeks.
In Asia and the Middle East, the differences are significant. In Singapore, MAS emphasizes actual control, while in Dubai VARA and local regulators require clear documentation of ownership. In the Czech Republic, Slovakia, Estonia and Cyprus the processes are formally straightforward, but banks supplement them with their own EDD. The COREDO team builds a unified package that equally convinces the registering authority and the bank officer.
Outsourcing vs in-house: sustainable model
The question “do it in-house or outsource” is decided by metrics. If the volume of onboarding and monitoring is high, and the client structure is complex, a hybrid model is often more effective: the internal team manages policies and risk level, while external specialists handle peak workloads and complex cases. Compliance services for UBO checks for corporations provided by COREDO include operational playbooks, training and tool implementation.
Shared utilities and centralized registries: a logical future. Corporate registries and interoperability will reduce the costs of duplicated checks, but there’s still a way to go before unified standards. For now, the winner is the one who can link different sources, maintain entity resolution and support real-time screening where it is critical for payments and correspondent settlements.
Monitoring changes in ownership structure
Monitoring changes in ownership structure and UBO is a process, not an event. I set an SLA for data updates: changes to the EU register of beneficial owners and to bank dossiers within specified business days. Include triggers: new shareholders, director changes, emergence of nominee services, trust relocation, material M&A transactions.
Banks value transparency and predictability. If a company announces a restructuring in advance and provides a package of documents, the risk of account freezes is noticeably lower. In one project, a solution developed at COREDO automated bank and registrar notifications via RPA, reducing the update cycle from weeks to days.
Common mistakes: how to avoid them
The first mistake: underestimating nominee structures and front owners. The bank will spot it if the beneficial owner is “hiding” behind a service company without a business reason. Second: incomplete information on trusts and funds: ignoring the protector, failure to provide a letter renouncing bearer shares, lack of description of beneficial interest. Third — lack of a documented source of funds for the UBO.
How to reduce onboarding time during UBO checks? Assemble the package in advance, use BODS standards and formalized structure diagrams, note sanctions and PEP checks, attach an adverse media report. Our experience at COREDO has shown that a proactive approach reduces the number of follow-up requests from the bank by 30–50% depending on the jurisdiction.
Conclusions: what to do next
By 2026, UBO registries and the practice of bank monitoring will ultimately set a new standard for working with ownership. This is not just a compliance requirement, but an element of competitiveness: you open accounts faster, get licenses faster, close deals faster. The role of UBO registries in the fight against money laundering will continue to grow, and along with it: expectations regarding data quality, their provenance and operational discipline.
COREDO was created to connect clients’ strategies with real regulatory practices in the EU, the United Kingdom, the Czech Republic, Slovakia, Cyprus, Estonia, Singapore and Dubai. I see how well-designed UBO processes, supported by technology and clear playbooks, turn the “pain” of compliance into a scalability advantage. Going forward, those who embed the UBO circuit into their business architecture will win: from company registration to bank onboarding and day-to-day operations.
UBO Registers 2026: public vs closed
By 2026, the geography of beneficial owner registers has become more predictable, but remains uneven in accessibility and quality. Public registers speed up banks’ UBO due diligence. On the other hand, strict GDPR constraints and differences in legal basis create “compatibility with friction” between countries and banks. Closed and governmental registers provide better accuracy and depth, but add latency and require formalized requests and justification of lawful basis.
Institutional interoperability is growing thanks to the Beneficial Ownership Data Standard (BODS) and the Open Ownership platforms, but the standard’s implementation is uneven. Where national corporate registers are synchronized with UBO records and use BODS, banks gain in time to onboard and reduce FPR without losing TPR. Below: a practical comparison.
Public vs closed UBO registers affect bank SLAs differently. Publicity speeds up initial checks and reduces the volume of client inquiries, but requires careful handling of personal data. Closed registers create a reliable basis for EDD and FIU investigations. At the same time, banks must plan time buffers in advance and formalize the routing of requests through competent authorities.
Regulatory framework 2026: UBO checks
The regulatory map for 2026 relies on FATF Recommendations 24/25 on the transparency of legal persons and trusts, the AMLD5/AMLD6 directives and national transpositions. In the USA the Corporate Transparency Act (CTA) operates with Beneficial Ownership Information (BOI) reporting to FinCEN and access regimes for financial institutions. In the EU a horizontal AML regulation is being formed at the same time and control over the quality of registers is being strengthened, which directly affects banks’ KYC procedures and the checking of UBOs in offshore jurisdictions.
GDPR defines the lawful basis for banks’ access to UBO personal data, and this is a practical matter, not theory. Banks most often rely on Art. 6(1)(c) “compliance with a legal obligation” and Art. 6(1)(f) “legitimate interest”, supplementing them with internal DPIAs and data minimization policies. Special categories of data require a separate analysis, and for cross-border transfers, mechanisms compatible with EU standards and local privacy laws.
The consequences of non-compliance are already tangible both financially and reputationally. Fines, mandatory SAR reports, unplanned regulatory audits and de-risking by correspondent banks are becoming a reality for companies that ignore beneficiary disclosure or manipulate nominee structures. My recommendation remains unchanged: document every part of the chain of control and keep the evidence package “on the shelf”.
Practical compliance checklist for UBO checks
- Define thresholds and control: record the ownership percentage, veto rights, shareholders’ agreements and actual influence on management. Prepare a written justification of the beneficial interest and attach a legal opinion if there are gray areas.
- Record the lawful basis: specify the GDPR basis, describe the bank’s role as controller and collect consents where necessary. Add DPIA/LIAs and data minimization and retention procedures.
- Keep them up to date: set SLAs for updates in the national register and at the bank when UBOs change. Include RPA reminders and checkpoints for internal legal and finance teams.
- Prepare an EDD file: collect Source of Funds/Wealth, CSP letters, nominee agreements and confirmations of the renunciation of bearer shares. Conduct PEP/sanctions/adverse media screening in advance and attach the results.
- Log provenance: preserve sources, document versions and hash-based integrity checks. This will speed up responses to regulatory inquiries and internal audits.
How banks verify UBOs and KYC
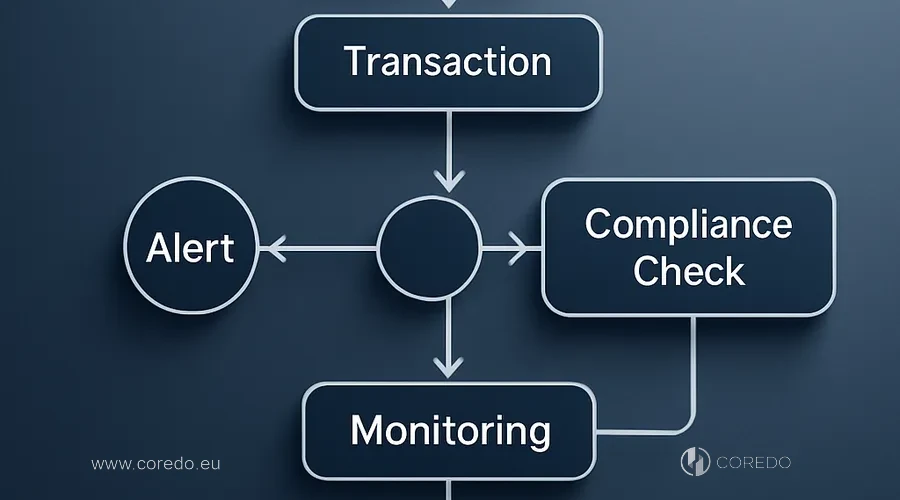
A bank KYC pipeline for UBO is a managed sequence of steps with clear owners. I advise clients to align their internal procedure to the same logic to shorten question‑and‑answer cycles and minimize false positives/negatives.
Step-by-step KYC pipeline
- Intake and pre‑screening: collection of the questionnaire, corporate documents and an initial description of the structure. Sanctions and PEP checks are run, as well as a quick adverse media review.
- Ownership mapping: building an ownership graph up to the ultimate beneficial owner, recording controlling rights and agreements. Threshold rules of 25% and 10% in the EU are applied, taking cumulative control into account.
- Documentary verification: matching registries, certificates and nominee agreements with client and provider data. A request is sent to the CSP and a formal reconciliation with local registries takes place.
- Screening and risk‑scoring: combining sanctions, PEP, negative news and geo‑risks into a single profile. ML models support entity matching and reduce FPR as TPR increases.
- Decision and onboarding: either standard approval, escalation to EDD, or rejection with justification. Results and provenance are logged for audit and correspondents.
Roles and responsibilities are allocated in advance and by name. The Relationship Manager gathers the package and manages communication, the KYC analyst handles the structural and documentary layer, the AML/Financial Crime team performs screening and risk‑scoring, and complex cases go to EDD/SME with the final decision by the Compliance Officer. Such a matrix reduces MTTR and provides predictability for the business and the client.
KYC pipeline diagram (textual)
Client intake → Pre‑screening → UBO mapping → Documentary verification → Sanctions/PEP/Adverse media → Risk‑scoring → Decision/EDD → Onboarding/Monitoring. Each stage records provenance and SLA, and integration points with registries go via API or formalized requests.
UBO verification in offshore jurisdictions
Офшоры привлекают гибкостью и скоростью, но для банка это маркеры повышенного риска. Nominee directors and shareholders, historical bearer shares, foundations and trusts, as well as a prominent role of CSP, all of this requires combined validation and a closer dialogue with the client. Чем раньше клиент покажет экономическую логику структуры и реальный контроль, тем ниже вероятность де‑райзинга.
Практические методики включают параллельную работу с несколькими контурами данных. Мы совмещаем локальные реестры, письма CSP, коммерческие агрегаторы, санкционные списки и adverse media, а затем подтверждаем транзакционным поведением, если счёт уже активен. Там, где трасты и фонды, особое внимание уделяем trust registers, распределению beneficial interest и ролям settlor/protector/beneficiaries.
Рекомендации банка и типичные red flags
- Применять EDD, когда структура включает nominee arrangements, трасты без прозрачной экономической цели, или страны с высоким риском по FATF. Дополнительно запрашиваются SoF/SoW, интервью с UBO и письма от независимых юридических консультантов.
- Красные флаги: несоответствия между реестрами и документами, частые смены директоров без бизнес‑обоснования, CSP без лицензии, и негативные news о связанных лицах. Такие сигналы активируют расширенный скрининг и могут привести к отказу.
Disclosure of beneficial interest
Идентификация nominee начинается с документов и не заканчивается ими. Банки запрашивают декларации nominee, договоры оказания услуг и подтверждение полномочий, а также правовые мнения о том, кто вправе распоряжаться голосами и дивидендами. Важно показать, что номинал не осуществляет самостоятельного контроля и действует строго по инструкциям бенефициара.
Мы всегда совмещаем документальный слой с данными о поведении и транзакциях. Если фактические платежи, подписи и IP‑логи инициируются одними и теми же лицами, это поддерживает картину бенефициарного контроля. Когда наблюдается расхождение между ownership data и транзакционным профилем, кейс уходит в EDD, и банк запрашивает дополнительные подтверждения beneficial interest.
EDD for UBOs: criteria and thresholds
EDD is triggered by a combination of risk factors, and this is normal practice for offshore structures and complex ownership. Classic triggers: PEP status of the UBO or key directors, high‑risk or sanctioned jurisdictions, structural complexity with trusts/funds/nominees, and discrepancies between registers and the documents provided. In the EU banks increasingly rely on a 10% threshold for UBOs in the EU in complex structures, even if the formal general threshold remains 25%.
Standard EDD procedures are detailed and resource‑intensive, so it is better to prepare for them in advance. Extended SoF/SoW packages, bank references, tax returns, asset sale agreements and interviews with the owner—where the structure’s motivation and sources of capital are discussed—are requested. In offshore jurisdictions a letter from the CSP about the nominee, confirmation of the renunciation of bearer shares and legal opinions on trusts and foundations are almost always required.
Examples of EDD scenarios
A Jersey trust with investments in the EU and a UBO resident of a third country. The bank will request the trust deed, letter of wishes, a list of beneficiary classes, documents on the protector and the founder’s SoW, as well as sanctions and PEP screening of all related parties.
A BVI holding with a nominee shareholder and operating companies in the EU. They will request the nominee declaration, the agreement and confirmation of control over votes, CSP letters, the shareholder register and confirmation of cash flows from the operating companies to the owner.
A PEP link for a minority owner with 12% in the EU. They will apply the 10% threshold, carry out enhanced adverse media checks, conduct an interview and request independent sources of income and an explanation of the business role.
Cross-verification of UBO registries
Reliable due diligence relies on the right mix of primary and secondary sources. National registries and trusted corporate registers form the “gold standard”, while OpenCorporates, Open Ownership, commercial aggregators and sanctions lists provide breadth and speed. Cross-verification through entity matching, fuzzy matching and reconciliation resolves contradictions and documents data provenance.
Table: data sources – advantages, limitations, update, reliability
| Источник |
Преимущества |
Ограничения |
Обновление |
Reliability |
| Национальные UBO‑реестры |
Official status and legal force |
Limited access and GDPR barriers |
T+1/T+15 |
High with proper query |
| Корпоративные регистры |
Confirm directors and participants |
Do not always include UBOs |
T+1/T+7 |
Medium-high |
| OpenCorporates |
Wide coverage and convenient search |
Heterogeneity and incompleteness |
Near real-time |
Medium |
| Open Ownership/BODS |
Structured relationships and standards |
Depends on connected registries |
Near real-time |
Medium |
| Коммерческие агрегаторы |
Speed and normalization |
Cost and algorithmic black boxes |
T+0/T+1 |
Medium-high |
| Санкции/PEP |
Regulatory criticality |
Varied formats and update latency |
T+0/T+1 |
High when multi-listed |
| Adverse media |
Early risk detection |
Noise and risk of false positives (FPR) |
Continuously |
Medium when tuned |
Cross-verification mechanics must be formalized and reproducible. We use entity resolution with canonicalization of names, addresses and identifiers, fuzzy matching to recognize transcriptions and aliases, and then run reconciliation against an internal “golden profile” and the client’s documents. This approach reduces MTTR and prepares the data for automated solutions and organizational audits.
Integration of registry data via ETL
A correct ETL pipeline for UBO data starts with ingestion via API and batch channels, then normalization according to BODS and local schemas, enrichment with sanctions and PEP data, and matching to already known entities. It’s important to log every transformation, store sources and versions, and also maintain re-validation on schedule and on triggers. At COREDO we additionally hash document versions and write provenance to immutable storage to simplify audit defense.
Best practice: separate the operational layer and the analytical data layer. The operational layer serves real-time screening and onboarding, while the analytical layer handles periodic reconciliation, reporting and ML training. This reduces the risk of SLA degradation and makes the system resilient to peak loads.
Automating UBO verification for banks
Automation tools are not a luxury but a necessity when scaling KYC. APIs for registry access, graph databases (Neo4j), link analysis and ML‑models for risk scoring form the core of the technology stack that accelerates UBO verification and improves quality. We see how real‑time screening and RPA workflows reduce manual work, and metrics MTTR, FPR and TPR become manageable.
Integration into the KYC pipeline requires an architecture with clear SLAs and monitoring. Queueing systems, retries, deduplication and observability (tracing/metrics/logs) reduce operational risk, and graph analysis helps uncover hidden links between transactions and ownership data. In several projects, graph features produced a jump in the accuracy of detecting nominee structures without increasing FPR.
Integration of API, real‑time and ETL
APIs must meet requirements for performance, security and compatibility with the BODS standard. We use JSON schemas, OAuth2/MTLS, idempotent keys and detailed error handling with typing and recovery codes. Implementing rate limiting and queues ensures even load and predictable SLAs even during peaks.
Best practices for real‑time screening and batch reconciliation include separating data paths and independently scaling resources. Real‑time serves the “decide here and now” needs for onboarding and payments, while batch addresses “quality debt” and checks profile consistency. Regular A/B tests of rules and ML models allow reducing FPR without losing TPR.
Correspondent Banks and Sanctions
Correspondent banks assess UBO risk through the lens of their own regulatory exposure and reputational loss. If a client’s profile combines an offshore structure, weak documentation and adverse news, the likelihood of de-risking rises sharply. Strong UBO documentation and pre-agreed EDD packages: the best protection against sudden shutdowns.
A de-risking case and lessons
- An international bank cut the correspondent line to a fintech with an offshore holding after a series of adverse media publications and a delayed UBO update in the national register. The client lost access to dollar payments for six weeks while assembling an EDD package and agreeing a lawful basis for access to closed records.
- We restored access through a package: an updated structure map, CSP letters, confirmed SoF/SoW, graph analysis of connections and an independent legal opinion on the trust. The bank accepted a remediation program and lowered the client’s risk scoring from “high” to “medium” on the condition of quarterly monitoring.
Practical tips for clients
- Prepare a “correspondent folder”: sanctions provisions, UBO structure in BODS format, SoF/SoW, screening results and the contact details of the responsible person. This speeds up responses and reduces uncertainty.
- Communicate proactively: notify structural changes and regulatory news before the bank asks. This builds trust and reduces the risk of preventive de-risking.
Implementing UBO procedures in a bank
Costs consist of data licenses, integration development, infrastructure, training, and operational support. In a typical bank, average TCO in the first year includes 40–60% of costs for data and APIs, 25–35% for development and integration, and 15–25% for operational processes and training, although proportions change with scale. I strongly recommend budgeting for data quality and ongoing reconciliation, because that is where MTTR is reduced and onboarding time is shortened.
Profitability is measured through a set of applied metrics related to business value. Reducing time to onboard by 30–50%, lowering FPR by 20–35% and stabilizing correspondent relationships are direct drivers of ROI that the C-level and the board understand. For multinational companies the effect is amplified if you use shared utilities, centralized registries, and a hybrid outsourcing vs in-house model with strict SLAs and KPIs.
KPI for UBO AML checks
Measurability is the foundation of a mature compliance function. We track TCO per case, time to onboard, MTTR on escalations, FPR/TPR of screening, the share of cases in EDD and the percentage of document returns. The formulas are simple and practical: FPR = FP/(FP+TN), TPR = TP/(TP+FN), MTTR: the median time from escalation to resolution, and ROI: share of OpEx savings plus revenue preserved from faster onboarding minus investments.
Quarterly targets should be ambitious but achievable. I often budget for -20% FPR while maintaining TPR, -25% time to onboard for standard cases and -15% MTTR for EDD thanks to templates and pre-checks. Such targets discipline the team and show the board of directors tangible progress.
Prepare the legal entity for the bank’s UBO request.
Proper preparation saves weeks and reduces stress for all parties. I recommend assembling three packages: corporate, beneficial and sanctions, each with versioning and provenance. Below is a consolidated checklist of documents by scenario.
| Scenario |
Core documents |
Additional (EDD) |
Notes |
| Onboarding |
Articles of association/formation documents, register of shareholders/members, UBO structure, UBO IDs and addresses |
SoF/SoW, CSP letters, nominee declarations, renunciation of bearer shares |
BODS format will speed up processing |
| Trusts/funds |
Trust deed, letter of wishes, list of beneficiaries, protector/settlor documents |
Legal opinion on control, tax statuses, extracts |
Disclose beneficial interest by class |
| Offshores |
Certificate of incumbency, register of members/directors, CSP letter |
Nominee agreement, confirmation of voting rights and dividends |
State the economic rationale of the structure |
| M&A |
Data room with structure, minutes/SPA, cap table, UBO matrix |
EDD report, sanctions/PEP, adverse media |
Speed diligence requires ready-made templates |
Recommendations for registrations in the EU/Asia are simple and effective. In the EU, pre-synchronize the UBO record with bank onboarding and licensing, and in Singapore and Dubai arrange with the CSP the timing and format for issuing UBO documents for banks. Before submission the CFO should go through an internal checklist, ensure registers are up to date, and run a test sanctions/PEP/adverse media report.
UBO verification in M&A and transactions
UBO‑due diligence in mergers and acquisitions – это speed diligence с акцентом на контроль и санкционные сопряжения. Мы строим ускоренный граф владения, валидируем бенефициарный интерес, проверяем скрытые соглашения акционеров и оцениваем риски де‑райзинга у банков‑партнёров покупателя. Чем раньше покупатель покажет план ремедиации структуры под требования AMLD6 и корреспондентов, тем ниже скидка на риск в цене сделки.
Post‑deal мониторинг должен быть автоматизирован и связан с триггерами изменений. Смена директоров, перераспределение долей, назначение nominee или переезд траста запускают переоценку риска и при необходимости, EDD. Мы используем RPA для оповещений регистраторов и банков и графовые подписки для сигналов о новых связях в adverse media.
Practical templates for the deal
- UBO‑request list: структурированный перечень документов, включая BODS‑выпуск и карту контроля. Он экономит время юридических команд и снижает количество уточнений.
- Risk‑скоринг владельцев: модель приоритизации проверок с весами по юрисдикциям, санкциям, PEP и сложностям структуры. Она помогает фокусировать EDD там, где это действительно нужно.
Recommendations for C-level executives and owners
I’ve compiled a focused ten-point checklist to help prepare for banks’ UBO checks.
- Structure map in BODS and as a graph. Keep it current and version it for audit.
- A single UBO document package with provenance. Update it with every change and register SLAs.
- Preliminary sanctions/PEP/adverse media screening. Catch issues before the bank sees them.
- Nominee and trusts policy. Document the economic rationale and boundaries of control.
- SoF/SoW for UBO. Prepare evidence in advance and store independent confirmations.
- Data quality and entity resolution. Implement normalization procedures and reconciliation of sources.
- API integrations and RPA workflows. Reduce manual work and ensure process observability.
- Metrics and targets: time to onboard, MTTR, FPR/TPR. Link them to bonuses and performance management.
- Correspondent ‘folder’ and playbooks. Maintain trust with banking partners and reduce the risk of de‑risking.
- Remediation plan under AMLD6/CTA. Update structural arrangements for new rules and jurisdictions.
Investments should be prioritized on the principle “data and automation first”. The tech stack for registry access, graph analytics and ML scoring pays off faster, while manual EDD remains for complex cases and model labeling. Outsourcing makes sense for peaks and niche expertise, but policy and risk appetite should remain in-house.
Frequently Asked Questions
Question 1: What is a UBO and which thresholds apply in 2026?
Answer: UBO, the ultimate beneficial owner, controlling the company directly or through a beneficial interest. The general ownership threshold of 25% is supplemented by a 10% threshold in the EU for complex structures and high risk, as well as by analysis of de facto control beyond shareholding.
Question 2: How do banks verify UBOs in offshore jurisdictions and which documents are most often requested?
Answer: Banks compare local registers, CSP letters, corporate documents and trust agreements, then perform sanctions/PEP/adverse media screening. Most often they request a certificate of incumbency, register of members/directors, trust deed, nominee declarations, renunciation of bearer shares and confirmations of SoF/SoW.
Question 3: What to do if a UBO does not disclose information or there is a nominee?
Answer: Prepare legal opinions and nominee declarations confirming absence of independent control and demonstrate the economic rationale of the structure. If disclosure is refused, the bank will likely apply EDD or refuse the relationship, so it’s better to proactively provide the maximum evidence of beneficial interest.
Question 4: How does GDPR affect a bank’s access to UBO registers?
Answer: The bank relies on Art. 6(1)(c) and Art. 6(1)(f) GDPR, supplemented by a DPIA and a minimisation policy. For cross-border data transfers compatible mechanisms are used and all requests and justifications of the lawful basis are logged.
Question 5: How much does it cost to implement automated UBO checks?
Answer: Costs depend on scale, but in the first year the lion’s share goes to licenses and integrations, and thereafter the main effect comes from reduced FPR and time to onboard. In typical cases payback is achieved within a 9–18 month horizon due to OpEx savings and preserved correspondent lines.
Conclusion
The year 2026 cements a new standard of transparency: UBO‑registers become an integral part of business architecture and banks’ KYC. Winners are those who combine the regulatory framework, high‑quality data and automation, and who prepare a convincing narrative of control and source of funds for each beneficiary. This approach reduces the risk of de‑risking, speeds up onboarding and increases resilience to regulatory shocks.
Your next steps are clear and achievable. Conduct an internal audit of UBOs and update the structure map in BODS format, assemble a package of documents with provenance and set up API integrations with key registries and aggregators. If you need to accelerate the process, contact our COREDO team: we will carry out an express readiness diagnostic, share document templates and help implement the technology stack for your processes and jurisdictions.